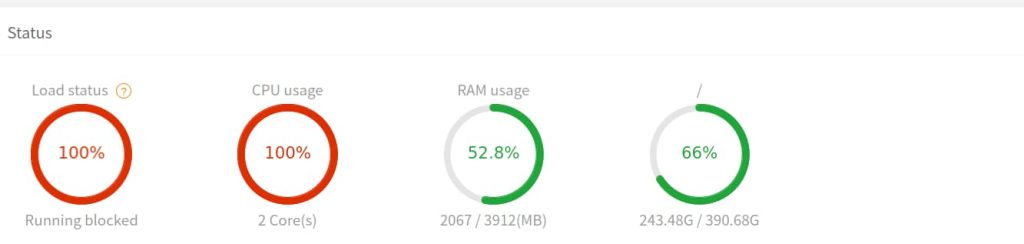
If you are experiencing frequent downtime on your VPS server, it might be that it is overwhelmed by the number of page requests for a given time. If that number is too high, it will cause delay in the server response time or even complete blackouts. In my case, for the last 30 days i was experiencing frequent server downtime and at one point I was not able to open any of the sites on my VPS server. In addition to that, when I opened aaPanel, i was greeted by these alarming red numbers and the whole server was terribly slow or not responding at all
A good practice to see what is causing downtime is to run the top command on your server. The processes that are the most CPU-intensive will appear on top. In my case, i quickly identified that the problem was in php-fpm, so I went on to check the php slow log and it showed me that the problematic requests that are causing the downtime are being made by bots rather than humans. To check the php slow log in aaPanel, you can go to App Store, php, settings and click on the php slow log tab. I saw that various requests to open files like .xmlrcp.php .wp-config.php or .wp-load.php in less than a second. A real site visitor would never attempt to open these files via a browser, as well as execute computations in an attempt to include these files in an external script and compromize my web server. After some reading on the topic, I realized I was a victim of frequent brute-force attacks. Since my VPS server is on a cheap plan, it does not have many resources – only 4GB RAM and 2 Core CPUs. So, in my case, these brute-force attacks were functioning like de-facto DoS (Denial of Service) or DDoS (Distributed Denial of Service) attacks. Needless to say, the first thing you should do in that case is to protect the above-mentioned files from direct access via a web client by amending the apache httpd file
<FilesMatch "(wp-config\.php|wp-load\.php|xmlrpc\.php)">
Require all denied
</FilesMatch>You can also consider restricting direct access to other sensitive files like the .php files inside the wp-includes folder. In addition to that, a good practice is to also enable mod_evasive in your web server configuration. Mod_evasive is one of the most efficient methods against brute-force and DDoS attacks because it limits the number of requests that can be made from a single IP address. How mod_evasive works is it temporarily blacklists an IP that has made too many requests to your web server for a given time. After the time has passed, the IP is enabled again until found “guilty” again.
How to install Mod Evasive in AaPanel
Installing mod_evasive in aaPanel that uses apache web server is not a straightforward process because you need to add this module manually. AaPanel does not have a built-in feature to install non-default apache modules. There are a few internet tutorials on how to install mod_evasive on Ubuntu but they are of no help here, because aApanel uses a custom Apache configuration and does not take advantage of the apache2-utils that can be installed on Ubuntu. The only way I managed to install and configure mod_evasive in aaPanel was to download the source code and install it manually. Here is what you should do in order to protect your web server from requests that cause frequent downtime to your server.
1. Navigate to your Apache modules folder
cd /www/server/apache/modules 2. Download mod_evasive source code
We will use the GitHub repository for that
wget https://github.com/jzdziarski/mod_evasive/archive/refs/heads/master.zip3. Unzip the file
unzip master.zip
cd mod_evasive-master4. Compile the module
First, make sure apache2-dev or equivalent is installed, as it contains headers and tools to compile Apache modules. If it’s not installed, you can install it using the following:
sudo apt-get install apache2-devAfter that, compile and install the module:
/www/server/apache/bin/apxs -i -a -c mod_evasive20.cNow, on apache>=2.4, the mod_evasive module will throw an error remote_ip is not found. Open the module’s source code and replace error remote_ip with client_ip. You can use nano editor or open it directly from aApanel web interface. Search and replace all occurences.
nano mod_evasive20.c
If you have updated the source code, make sure to recompile the module again:
/www/server/apache/bin/apxs -i -a -c mod_evasive20.c
5. Restart Apache
sudo /etc/init.d/httpd restart6. Include mod_evasive in apache config file
Open apache httpd file (in aaPanel, you can go to App Store, apache, setting, configuration and add mod_evasive here:
LoadModule evasive20_module modules/mod_evasive20.soYou also need to add the mod_evasive configuration here. Add it after you have loaded the module. Here is an example configuration. You can adjust the numbers but take into account that too restrictive numbers can block valid users.
<IfModule mod_evasive20.c>
DOSHashTableSize 3097
DOSPageCount 5
DOSSiteCount 40
DOSPageInterval 1
DOSSiteInterval 1
DOSBlockingPeriod 7200
DOSLogDir "/www/server/apache2/logs/mod_evasive.log"
</IfModule>DOSPageCount determines how many requests a single IP can make to one specific page. DOSSiteCount regulates the number of allowed requests to any part of your website.
The above configuration allows up to 40 requests per second from the same ip. A number between 40 and 100 is legitimate because web pages can make many requests, i.e. css files, js files, etc.
Congratulations! If you followed this tutorial, you should have successfully installed mod_evasive on aaPanel and protected yourself from DDos and brute-force attacks.
